As you may already know, Zip files can be secured by a password to protect your files against unauthorized access. If you happen to forget your password, then this tutorial will definitely help you crack the password of that file using Linux tools.
In this guide, we will be using the two most convenient ways to crack a zip file in Linux, the first will be using JohnTheRipper and the second using fcrackzip tool.
By default, both tools are pre-installed in Kali Linux, so if you’re on Kali, you won’t have to follow the installation process we’ll show in this tutorial. However, if you’re on Ubuntu or Debian, you have to install them to proceed.
Before we dive into cracking our zip file, we gonna create our protected zip file. To do that, we’ll be using the zip command to create a password-protected zip file. Installing the tool first:
$ sudo apt update
$ sudo apt install zip
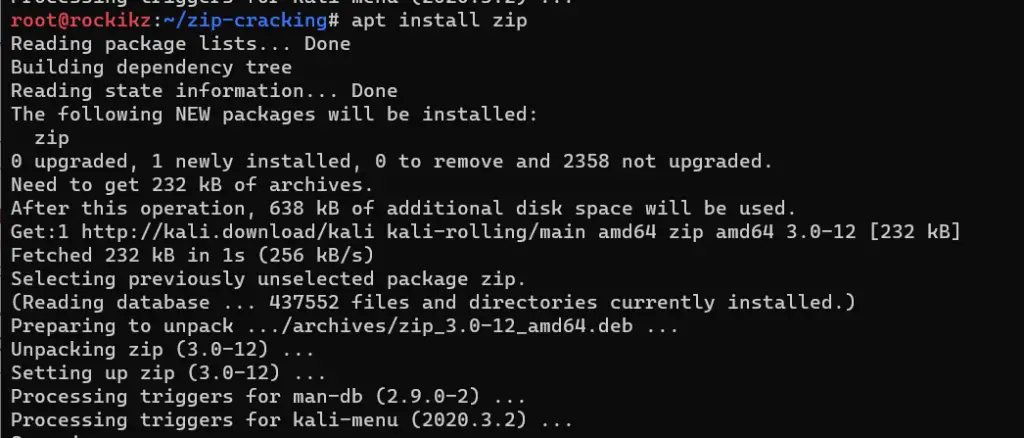
Next, make the zip file now:
$ touch file1
$ touch file2
$ touch file3
$ echo "this is file1" > file1
$ zip --password iamchampion secret.zip file1 file2 file3
adding: file1 (stored 0%)
adding: file2 (stored 0%)
adding: file3 (stored 0%)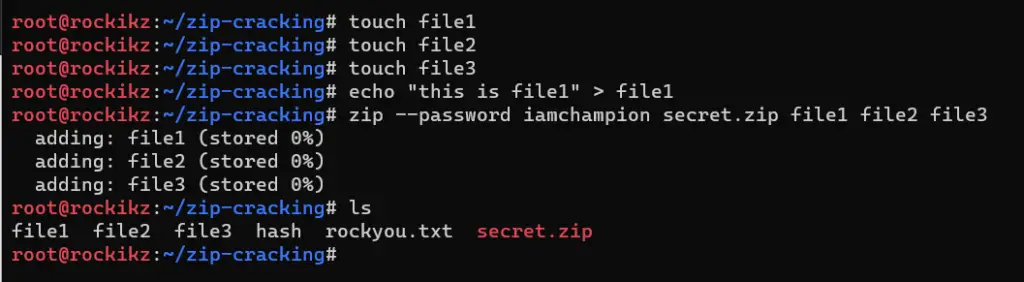
Now that we have our secret.zip file. In the upcoming sections, we’ll try to crack it using two different methods in Linux.
Method 1: John the Ripper
John the Ripper is a fast password cracker that is pretty much for everything that can be cracked offline, it is available in almost all operating systems.
If you’re on Kali Linux, it is pre-installed. Otherwise, let’s install the tool. First, make sure you created a folder in your system, naming it crack-zip:
$ mkdir crack-zip
$ cd crack-zipNext, cloning John the Ripper Github repository:
$ git clone https://github.com/openwall/johnThis will take a few seconds to a few minutes depending on your Internet speed. Next, let’s change the current directory to the src folder in JohnTheRipper parent directory:
$ cd JohnTheRipper/srcFinally, we update our repository, install the libssl dependency and install John the Ripper tool:
$ sudo apt update
$ sudo apt install libssl-dev
$ ./configure && makeAgain, this will take a few minutes depending on your network and CPU conditions. Give it some time and you’ll be ready to go. When it’s finished, get back to your original folder (crack-zip in my case):
$ cd ..
$ cd ..Now that we have installed our tool, let’s dive into cracking our previously created ZIP archive file.
First, we need to extract the hash from the zip file so we can compare the hash of the trial password with the hash of the real password. Luckily, the tool we just installed has the zip2john script that does just that:
$ JohnTheRipper/run/zip2john secret.zip > encrypted.hash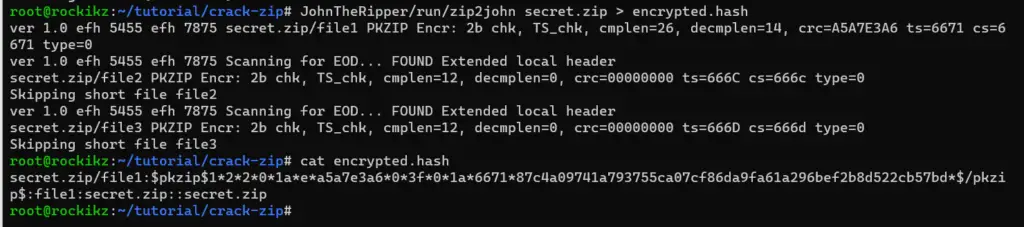
Note: If you’re on Kali Linux, you don’t have to run the zip2john from JohnTheRipper/run folder, you simply run the pre-installed zip2john command that is already added to $PATH.
The zip2john script that is located in the run folder has enabled us to extract the password hash from the secret.zip file into a new file named encrypted.hash.
Next, let’s crack the hash now:
$ JohnTheRipper/run/john encrypted.hash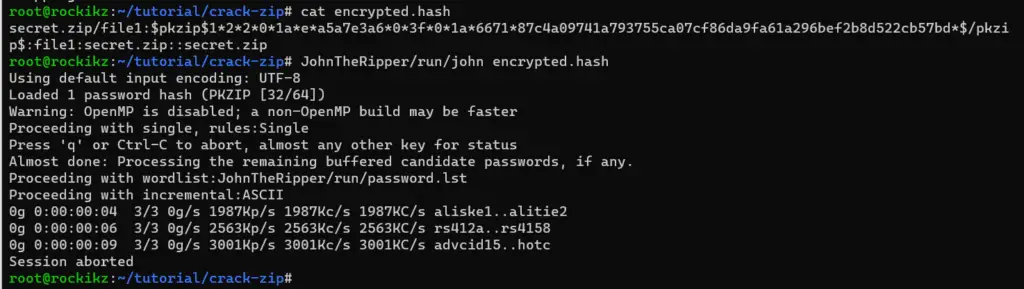
Note: If you’re on Kali, simply run john instead of JohnTheRipper/run/john.
As in the cracking PDF tutorial, the john tool will first try the default password.lst file located in the run folder. If it can’t find any matched passwords, it’ll go for incremental brute-force attack, which takes a lot of time.
You can cancel the cracking using the “q” or CTRL+C buttons. Any other key will print the current cracking progress.
We can specify the --wordlist argument to pass our customized wordlist. By the way, you can always use the crunch tool to create your customized wordlist, but we’ll be using existing ones such as rockyou.txt.
$ wget https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt
$ JohnTheRipper/run/john --wordlist=rockyou.txt encrypted.hash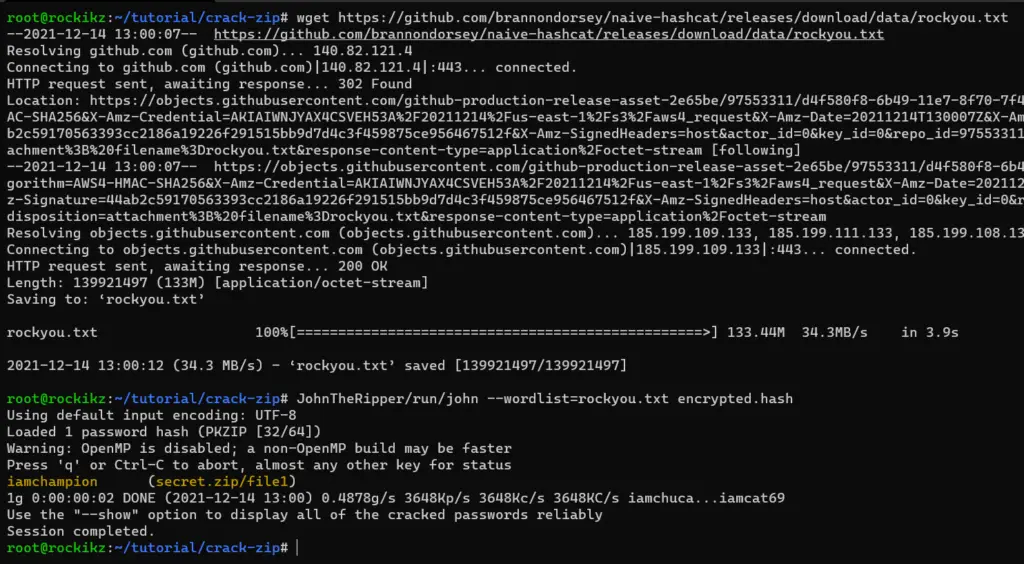
Again, if you’re on Kali Linux, the rockyou.txt wordlist along with other useful wordlists already exists in the /usr/share/wordlists folder in your system, make sure to simply unzip it and run the cracking instead of downloading it as I did in the above command.
As you can see, the password was successfully cracked and highlighted in yellow, it is "iamchampion" as we’ve made it earlier!
Note that the second time you run the same command will not show anything as it’s cached in the run/john.pot file. You can remove the --wordlist argument and use --show to show the already cracked password again.
Now that we have successfully cracked the password of a zip file using John the Ripper utility, let’s dive into the next method which is using the fcrackzip tool.
Method 2: fcrackzip
fcrackzip is a fast password cracker written in assembler and C, it is able to crack password-protected zip files with brute-force or dictionary-based attacks. It is definitely useful for pen-testers and ethical hackers.
Again, it comes pre-installed in Kali Linux. The below command is responsible for installing fcrackzip if it’s not already installed in your Linux machine:
$ sudo apt install fcrackzipLet’s pass --help to see various arguments this tool offer:
$ fcrackzip --help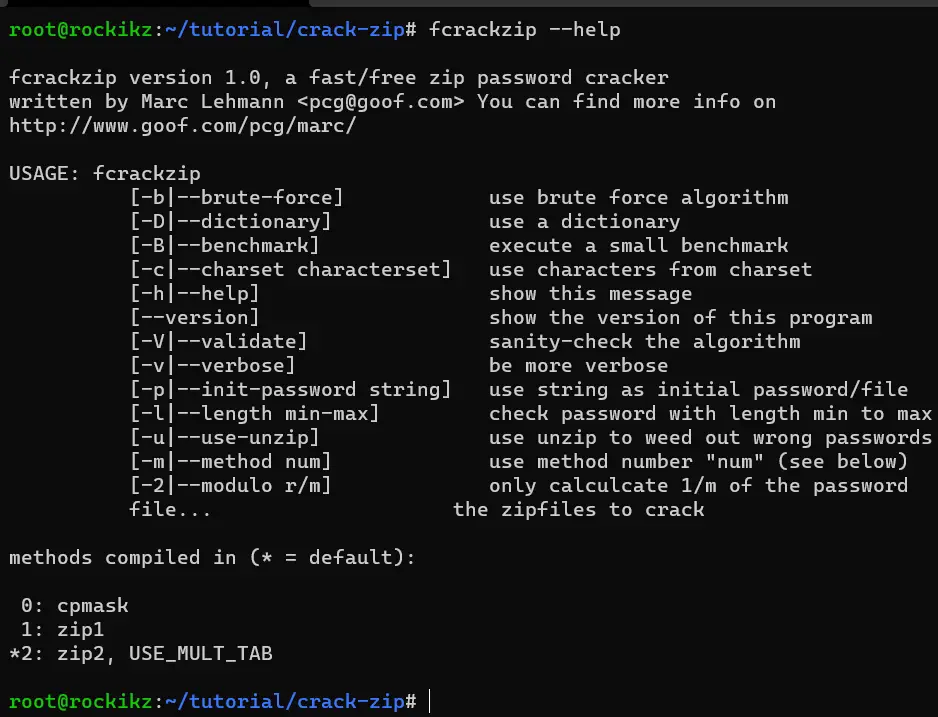
As you can see, we can either pass -b for brute-force, or -D for dictionary attack.
Let’s start off by brute-force attack:
$ fcrackzip -b -u -v secret.zip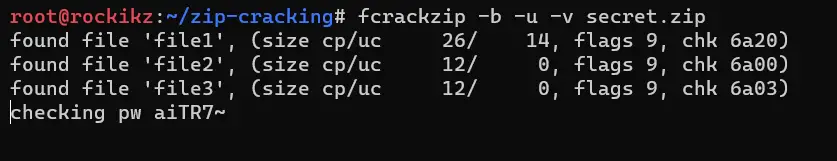
As you saw in the usage, I passed -b for brute-force attack, -u for eliminating wrong passwords, and -v for printing the current checked password, just to see the progress.
This will take decades to finish, simply because it’s starting from 'a' to infinity, we can pass the minimum and maximum length of the password by setting -l or --length argument:
$ fcrackzip -b -u -v -l 11-11 secret.zip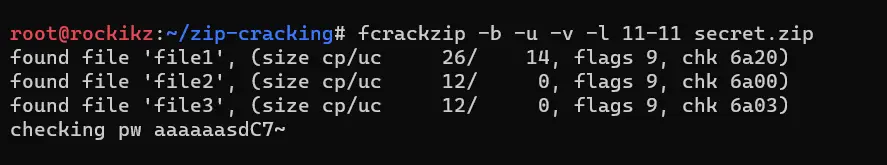
Since I know the password has a length of 11, I’m setting it, but you can set something like 8-20 to indicate 8 as minimum and 20 as maximum. This will still take years to finish using the most powerful CPU.
Next, we can pass the phrase to start brute-forcing from using -p:
$ fcrackzip -b -u -v -p iamchaaaaaa secret.zip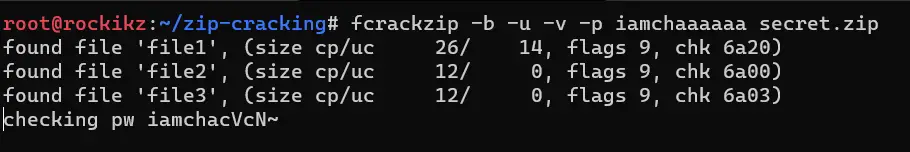
I have passed the starting phrase to be "iamchaaaaaa". After several seconds or a minute, the password is successfully cracked:
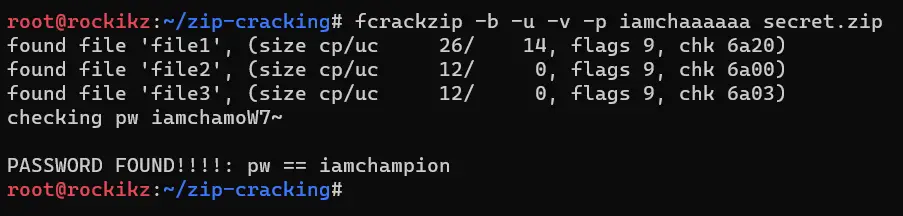
Not bad for a brute-force! You can definitely use this if you know there is a particular word in your password and forgot the remaining.
You can also use the -c or --charset argument to specify the character set.
Now we’re familiar with performing brute-force on zip files, let’s dive into dictionary attacks.
To pass a wordlist to fcrackzip, we simply use the -D option and pass the file name to the -p argument:
$ fcrackzip -D -u -v -p rockyou.txt secret.zip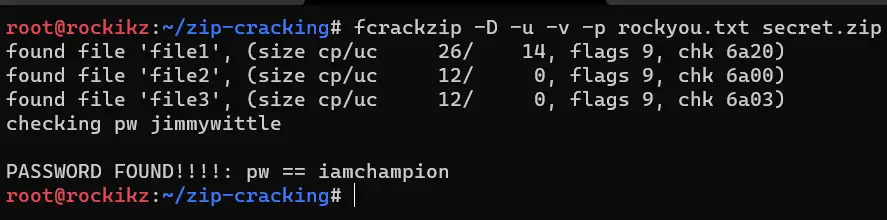
I found the password in a few seconds!
Conclusion
Alright, that’s it for the tutorial. I hope it was useful for you to crack your zip files in Linux. I highly suggest you type man fcrackzip to get further details on how to use the tool.
Regarding the John tool, there is a lot to explore in this tool and not just what we’ve seen, john --help or man john will allow you to see further information on specifying customized cracking.
Related tutorials:
- How to Brute-Force SSH in Linux
- How to Crack PDF Files in Linux
- How to Scan SQL Injection Vulnerable Sites using Sqlmap
Happy cracking ♥
