Securing your PDF documents is a good way to ensure that your PDF is safe and your privacy is retained. However, when using a weak or predictable password, you can easily be in the danger.
In this guide, you will realize how easy it is to crack PDF documents using two methods, one with the famous JohnTheRipper tool, and the other with pdfcrack.
Before we dive into cracking PDF passwords, I’m going to encrypt a random PDF file that I found on my computer. For that matter, I’m going to use the pdftk tool to add a password to this PDF document:
$ pdftk 1710.05006.pdf output encrypted.pdf user_pw password123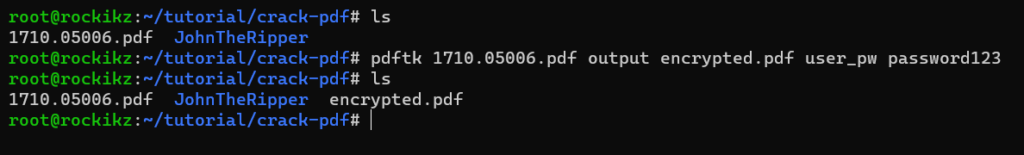
Now the encrypted.pdf file is an encrypted PDF document with the password password123.
Note: If you want to follow along, make sure to install pdftk tool using snap install pdftk command.
Method 1: John the Ripper
John the Ripper is a fast password cracker pretty much for everything that can be cracked offline, it is currently available in Linux, macOS, Windows, and many other environments.
Before we get started, we need to install the tool. First, make sure you make a folder in your system. I’m creating a crack-pdf folder:
$ mkdir crack-pdf
$ cd crack-pdfSecond, let’s clone the GitHub repository:
$ git clone https://github.com/openwall/johnThis will take a few seconds to a few minutes depending on your Internet speed. Next, let’s change the current directory to the src folder in JohnTheRipper parent directory:
$ cd JohnTheRipper/srcFinally, we update our repository, install the libssl dependency and install John the Ripper tool:
$ sudo apt update
$ sudo apt install libssl-dev
$ ./configure && makeAgain, this will take a few minutes depending on your network and CPU conditions. Give it some time and you’ll be ready to go. When it’s finished, get back to your original folder (crack-pdf in my case):
$ cd ..
$ cd ..Now that we have installed our tool, let’s dive into cracking our previously created PDF document.
First, we need to extract the hash from the PDF file so we can compare the hash of the trial password with the hash of the real password. Luckily, the tool we just installed has the pdf2john.pl script that does just that:
$ JohnTheRipper/run/pdf2john.pl encrypted.pdf > encrypted.hash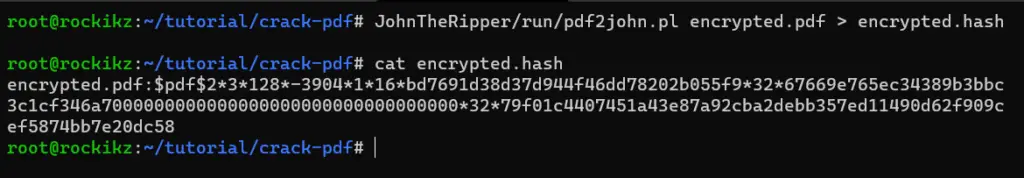
The pdf2john.pl Perl script file along with other very useful scripts are located in the run folder after you’ve successfully built and installed JohnTheRipper as shown previously.
As you can see, we have created another file named encrypted.hash that contains the hash of the target password of the encrypted.pdf file.
Let’s crack the hash now:
$ JohnTheRipper/run/john encrypted.hash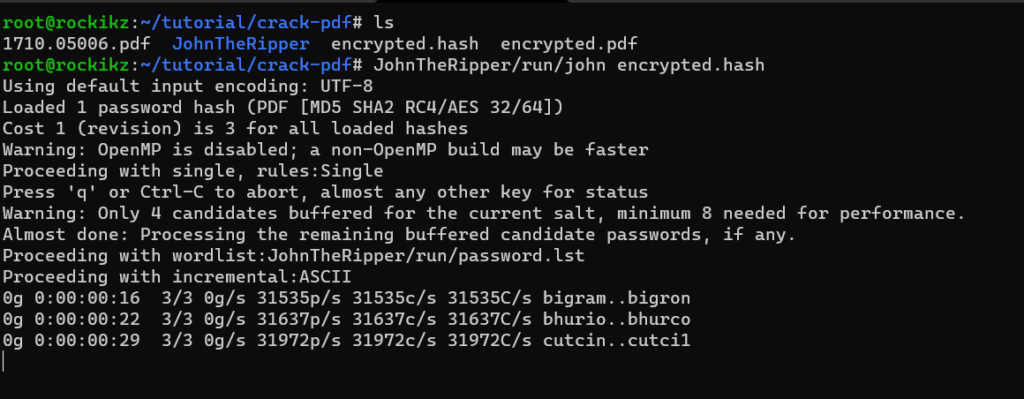
The john tool will first try the default password.lst file located in the run folder. If it can’t find any matched passwords, it’ll go for incremental (brute-force attack) which takes a lot of time.
You can press any button besides 'q' and CTRL+C (which stops the cracking) to show the progress. In my case, it is performing about 32k passwords per second.
We can specify --wordlist argument to pass our customized wordlist. You can use the crunch tool to create your wordlist, or use pre-existing ones such as rockyou.txt:
$ wget https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt
$ JohnTheRipper/run/john --wordlist=rockyou.txt encrypted.hash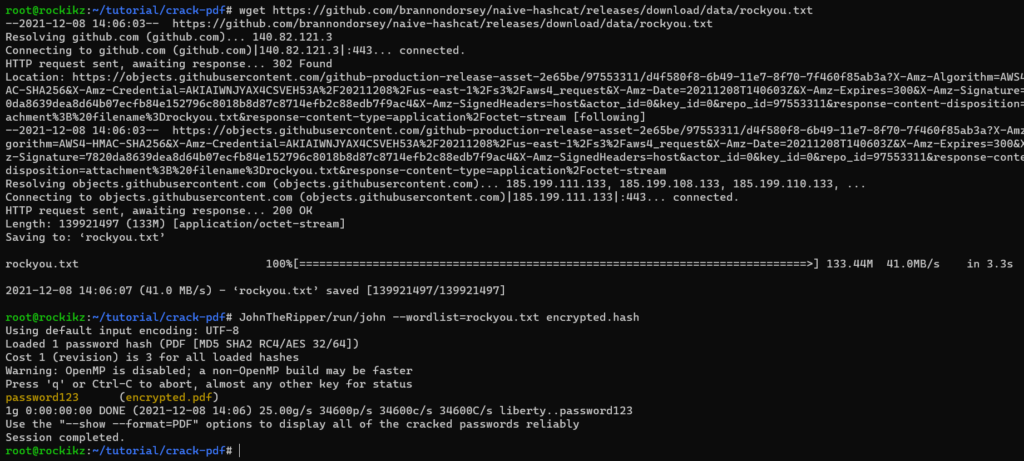
As you can see, the password was found and highlighted in yellow! and it is password123. The second time you run the same command will not show anything as it’s cached in the run/john.pot file. You can remove the --wordlist argument and use --show --format=PDF to show the password again after it’s successfully cracked.
Alright! You have successfully cracked the password of a PDF document using John the Ripper tool! In the next section, you will learn how to do that using pdfcrack.
Method 2: pdfcrack
PDFCrack is a simpler tool compared to John for recovering passwords from PDF documents, it should be able to handle all PDF files that are encrypted with a password. In this section, we’ll be using the same file we created earlier for cracking the password.
Installing pdfcrack is pretty straightforward:
$ apt install pdfcrackAfter that, you can use the tool right away. Writing the tool name as is will give us some help on how to use it:
$ pdfcrack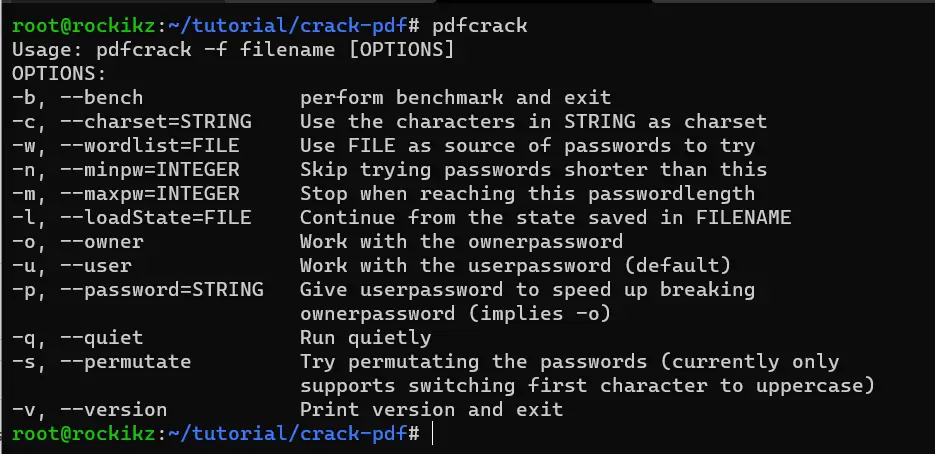
You can also type man pdfcrack for detailed information about the usage. Let’s crack the password of encrypted.pdf with the rockyou.txt wordlist:
$ pdfcrack -f encrypted.pdf --wordlist=rockyou.txt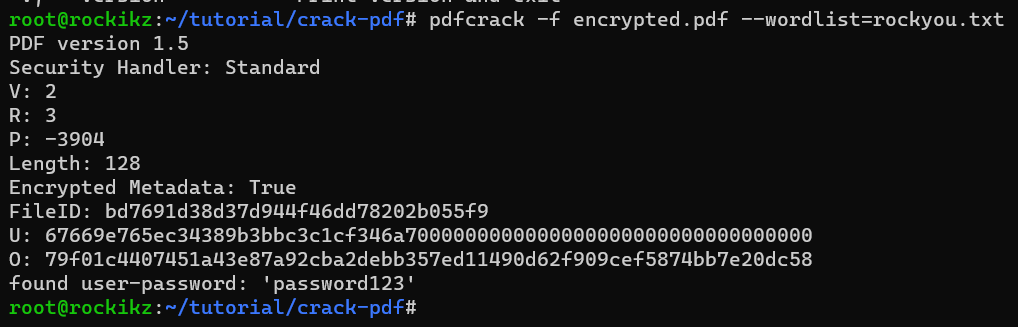
The password was found immediately after pressing Enter! By default, the tool uses brute-forcing, which means it tries all possible combinations of lowercased and uppercased ASCII characters along with numbers. Again, you can use crunch for advanced wordlist creation, or use the parameters of this tool such as --minpw and --maxpw to crack with a customized wordlist.
One of the cool features of pdfcrack is that you can resume a stopped job. If you CTRL+C to stop the cracking, a new file called savedstate.sav will be created in the current working directory for resuming purposes, if you run the command again, the tool will automatically continue where it left off last time.
Conclusion
Alright, that’s it for you! This guide shows the best two methods of cracking PDF documents in your Linux machine, make sure to pick the one that suits you best!
Learn also: How to Brute-Force SSH in Linux
