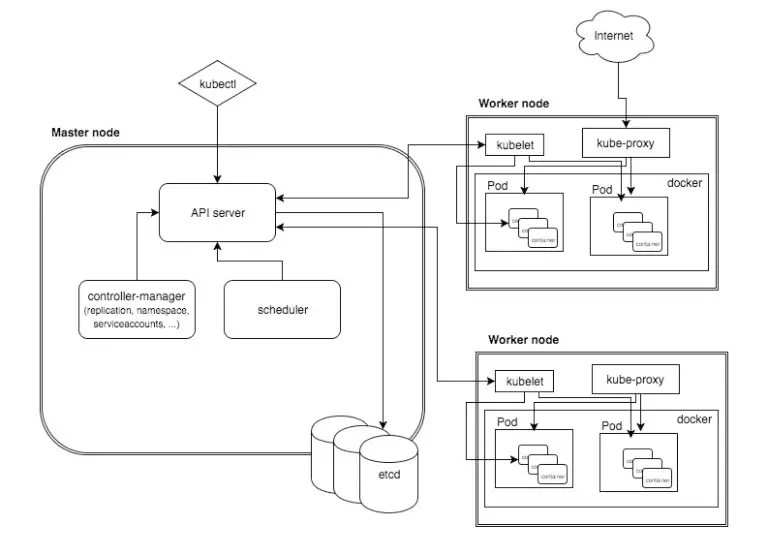
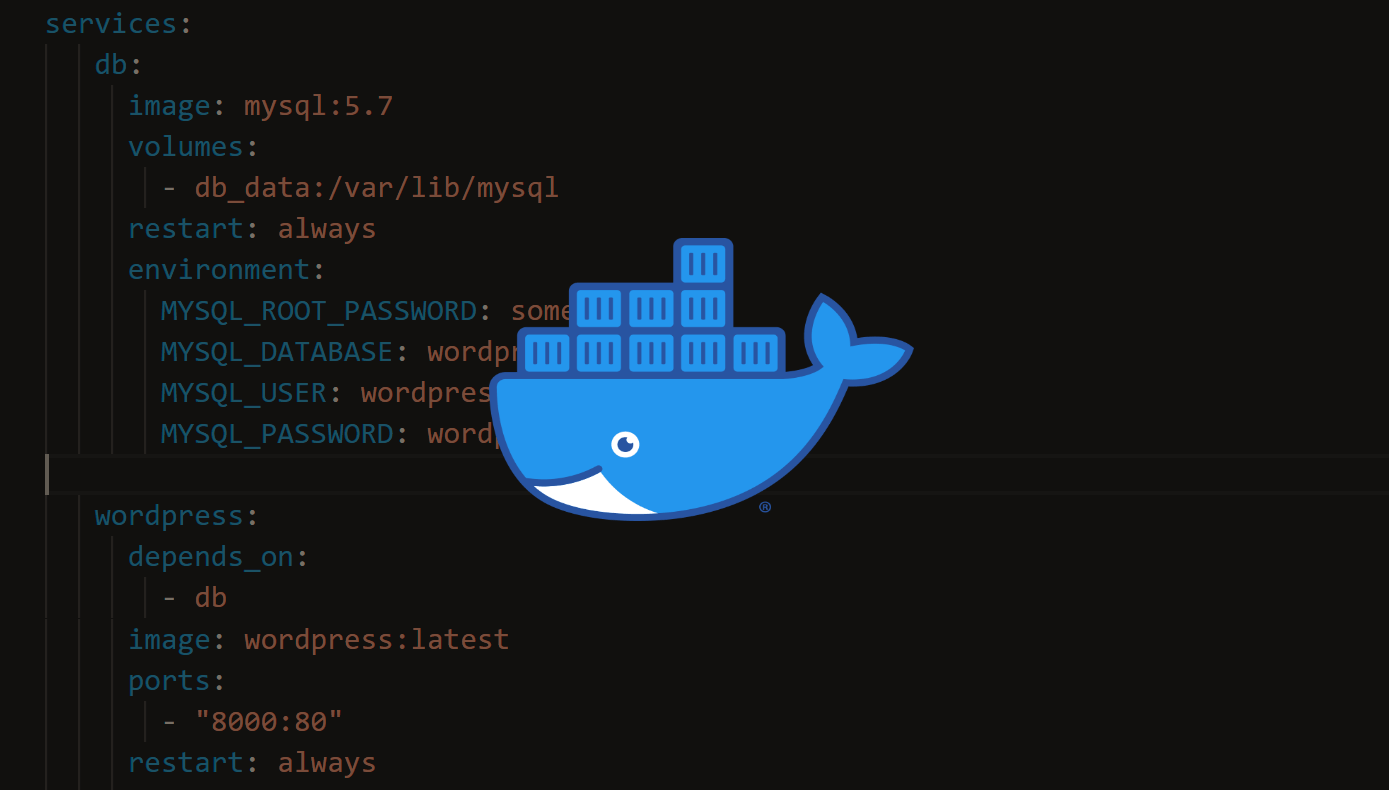
Introduction to Serverless Architecture
Serverless architecture, also known as serverless computing or function as a service (FaaS), is a software design pattern where applications are hosted by third-party service providers. They eliminate the need for server software and hardware management … Read more