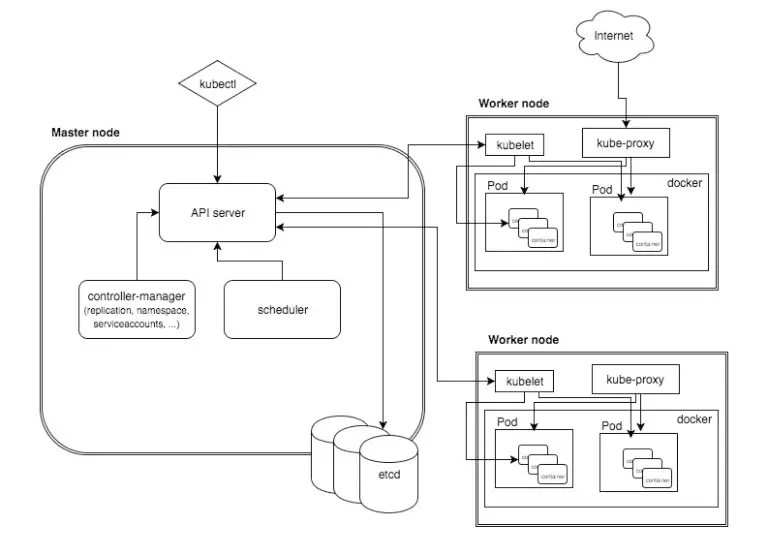
Introduction
Kubernetes is a cornerstone for the development of microservices SaaS and cloud-native software. Microservices necessarily need container technology and container orchestration since their architecture usually addresses a large number of containers.
In this context, the Kubernetes dashboard is the … Read more